Cloud Security and Vulnarability testing
How secure is Secure enough ?? Deep dive into known cyber attacks on cloud dervices
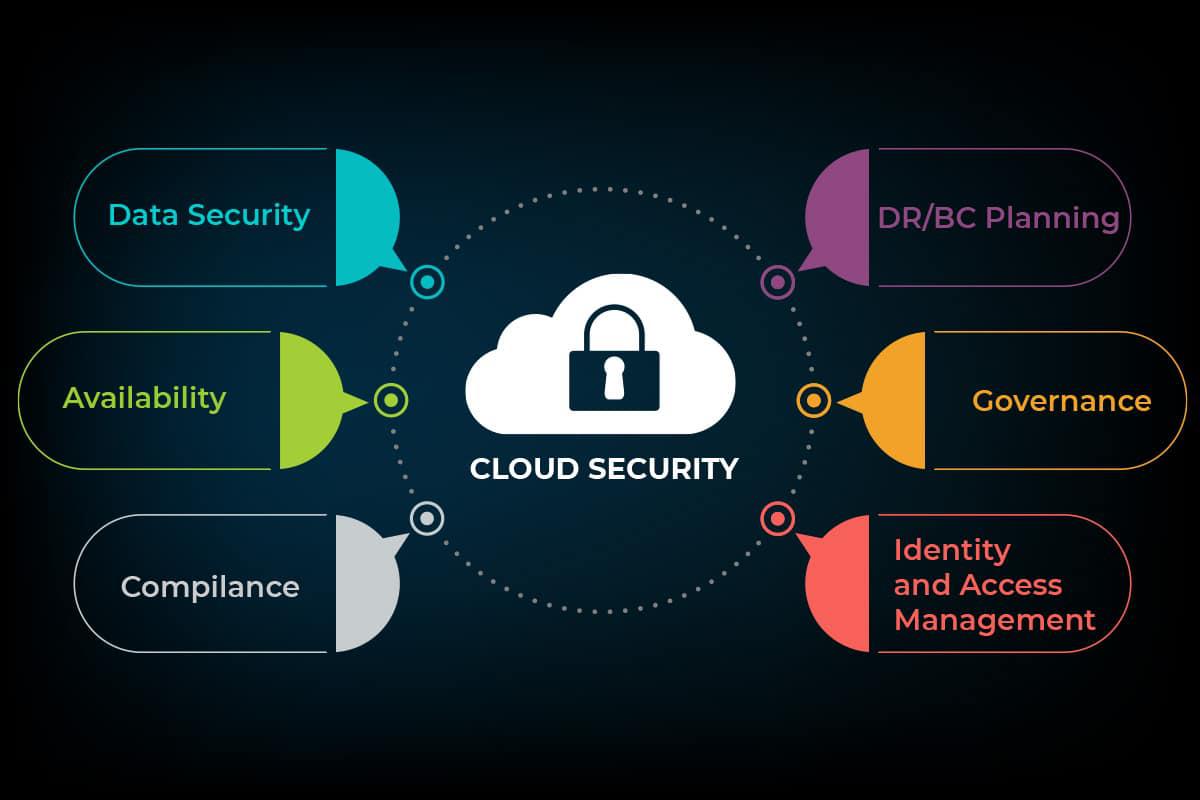
Keeping the cloud services up with bare minimum down time is a huge challenge.
A vulnerability assessment is a systematic review of security weaknesses in an information system. It evaluates if the system is susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed.
Examples of threats that can be prevented by vulnerability assessment include:
- SQL injection, XSS and other code injection attacks.
- Escalation of privileges due to faulty authentication mechanisms.
- Insecure defaults – software that ships with insecure settings, such as a guessable admin passwords.
There are several types of vulnerability assessments. These include:
- Host assessment – The assessment of critical servers, which may be vulnerable to attacks if not adequately tested or not generated from a tested machine image.
- Network and wireless assessment – The assessment of policies and practices to prevent unauthorised access to private or public networks and network-accessible resources.
- Database assessment – The assessment of databases or big data systems for vulnerabilities and misconfigurations, identifying rogue databases or insecure dev/test environments, and classifying sensitive data across an organisation’s infrastructure.
- Application scans – The identifying of security vulnerabilities in web applications and their source code by automated scans on the front-end or static/dynamic analysis of source code.
The security scanning process consists of four steps: testing, analysis, assessment and remediation.
In this article I will walk you through the complete all steps and perform security assessment of your cloud/datacenter/server using worlds most trusted tool, OpenVAS.
We will start by creating a ubuntu server and install the required tools. you will have four different services after successfully following the instructions,
- Greenbone Security Assistant, a graphical interface that allows you to manage vulnerability scans from a web application
- A database that stores results and configurations
- Regularly updated feed of NVTs (Network Vulnerability Tests)
- Scanner, which runs the NVTs
Install OpenVAS 9 on Ubuntu 18.04 LTS
Before we go to the installation part, we need to add the PPA repository to the system.
Step 1 – Add PPA Repository
Execute all commands in root user.
sudo add-apt-repository ppa:mrazavi/openvas
Step 2 – Update System
sudo apt-get update
Now we will install needed packages.
Step 3 – Install SQLite
SQLite is a C-language library that is the most used database engine in the world.
sudo apt install sqlite3
Step 4 – Install OpenVAS 9
Now is the time to install OpenVAS 9.
sudo apt install openvas9
It will ask to configure Redis Unix socket. Then select yes and continue.
 Redis Configuration
Redis Configuration
After the installation is done, you have to configure some packages.
Step 5 – Install other needed packages
For PDF reporting, we have to install some packages for it.
sudo apt install texlive-latex-extra --no-install-recommendssudo apt install texlive-fonts-recommended
We need the “openvas-nasl” utility which is provided by the “libopenvas9-dev” package to run OpenVAS NASL scripts against a target or sometimes troubleshoot and check NASL scripts for errors.
You can install it using the following command:
sudo apt install libopenvas9-dev
We will add the vulnerability data to the database by syncing with the feeds. It can be done using the following commands.
greenbone-nvt-syncgreenbone-scapdata-sync
 Data Sync
Data Sync
greenbone-certdata-sync
These syncs will get some time to update.
After the update is done, we can restart services.
Step 6 – Restart OpenVAS Services
Restart the OpenVAS scanner.
systemctl restart openvas-scanner
Restart the OpenVAS manager.
systemctl restart openvas-manager
Restart the Greenbone security assistant.
systemctl restart openvas-gsa
Then enable restarted services on system boot.
systemctl enable openvas-scannersystemctl enable openvas-managersystemctl enable openvas-gsa
Step 7 – Check OpenVAS processes
ps -aux | grep openvas
 Openvas Processes
Openvas Processes
Rebuild the NVTs cache and all synced feed will be loaded into the manager.
openvasmd --rebuild --progress
Step 8 – Verify Installation
Here we are going to use openvas-check-setup tool for checking the state of OpenVAS installation.
Download and copy it to your path:
wget --no-check-certificate https://svn.wald.intevation.org/svn/openvas/branches/tools-attic/openvas-check-setup -P /usr/local/bin/
Give execute permission.
chmod +x /usr/local/bin/openvas-check-setup
Now verify installation.
openvas-check-setup --v9
 Verify Installation
Verify Installation
Step 9 – Test Installation
Now everything is ok. We can browse the web interface. Open a browser and use the following URL.
https://Server-Ip:4000
The login default username and password is “admin”
 Web Interface Login
Web Interface Login
After login, you can see the Dashboard.
 DashBoard
DashBoard
Now we will add a scan target. So click on Scan-> Task. Then you will get the following window.
 Scan Task
Scan Task
Add target.
 Add Target
Add Target
Then start the scan and you will see scan is running.
 Scan In Progress
Scan In Progress
After the scan is completed, you can download reports in PDF format.
We successfully installed and configured Openvas9 on Ubuntu 18.04 LTS and added a target to scan. If you have any issue with the installation, feel free to discuss in the comments section below.
Gopal Jani
https://www.linkedin.com/in/gopal-jani/






No comments yet. Login to start a new discussion Start a new discussion